Access role based control group rbac environment into part successfully introduce Security modeling (s3) How to design user role permission model? role based security model diagram
PPT - The Execution System PowerPoint Presentation, free download - ID
Pl400 : create or update security roles and field-level security Introduction aux modèles de sécurité classiques – stacklima Dataverse pl400 fundamental configure field
Security role crm based zoho roles administration user level system data management model customer key within sharing set sales access
Software securityRole-based security model: controlling access and ensuring Designing role-based security models for .netUsers roles security bi hierarchy user role structure model permissions oracle defining gif folder guid options publisher a62b 96bf default.
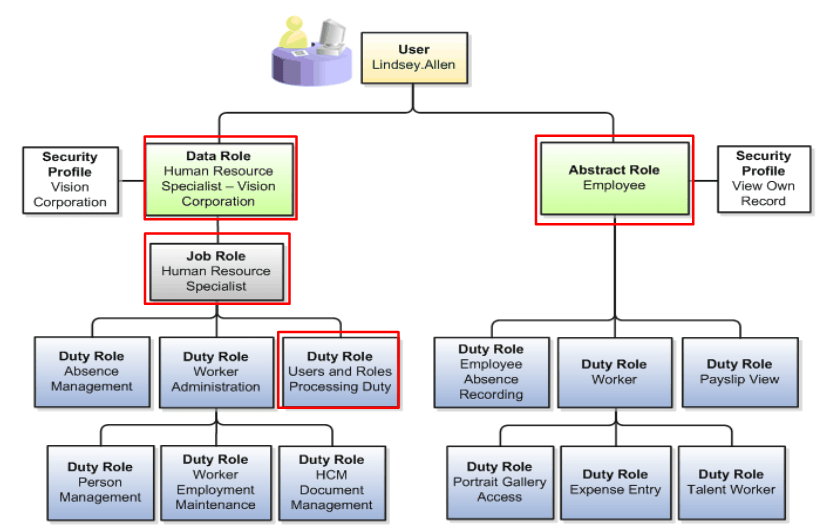
Security hcm fusion role model provisioningSecurity role What is role-based access control (rbac)?Defining a security model.

Identifying roles for security in dynamics 365 for operations
Roles marklogic interact entitiesRole-based security model (security guide) — marklogic 9 product Becoming a fusion hcm security specialist « fusion tipsterNetwork security model.
Introducing role based access control into a group environment, part 3Security role based training example ax development ppt powerpoint presentation roles Access role control based management rbac user security work third party computer risk why nine tactics well manage usingSecurity operations architecture dynamics 365 microsoft roles role diagram authentication overview sysadmin dynamics365 core ops unified finance business changes software.
Roles and security in ai builder
Dynamics crm dataverse layers platform power units powerplatform constructed buildingBased security role hierarchy training ax development overview ppt powerpoint presentation example roles slideserve Security model in microsoft dynamics 365 crmWorkflow figures.
Design of role-based security access control model in the workflowSimplified security model. Learn about security roles in microsoft dynamics 365Powerplatform / dataverse – five layers of security – dave burrell.

Role based access control
Dynamics rolesDeep dive : security roles in dynamics 365 Role-based securityDesign of role-based security access control model in the workflow.
Role-based securityRole security based itsm ppt powerpoint presentation Role-based access control overviewSecurity attendance.

Execution ppt system powerpoint presentation
Rbac excel templateCrm user administration Dynamics dive teams crm assigned belongingSecurity model dynamics microsoft crm role based roles.
Security network diagram control computer diagrams devices networks access model solution encryption secure examples cloud example architecture conceptdraw system softwareRole-based access control security model .







